How I was able to Download Any file from Web server!
Hello to all Masters and Learners,
I hope you all are doing well and spending most of your time in hunting and learning. Where most of us spend time to exploit the mechanism or to find out the weak endpoints. 😀
This is my first Write-up, I know that I am weak in English but I’m going to try my best to explain.
In past days I was hunting a private site I mean totally private. The site is not included in any bug bounty program.
It is a software Management site at which companies make their team to accomplish their tasks. At that time I knew nothing about the RECON Phase which is
most important while hunting/pentesting the site.
At first I tried some XSS payloads and successfuly popup an alert.

I made a video POC and Reported to them.
After some conversation with their team i got a $150 reward for it.

Reward boost me up! again to test the site and at that time i again tried some XSS payloads at different endpoints and executed Successfully in it :D. I don’t want to exposed how many it was 3:)

As i told you the site is for managing the software tasks so there is an option to upload files. These files are only shown to your team members. As i was testing for XSS so i tried to upload a file that contained an XSS Payload.
(WordPress don’t allow to post payload even in Base64 encoding :/ so i paste a picture)
The Payloads that I mostly use is
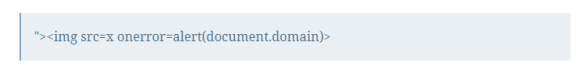
but some time I also try

actually it’s depend upon the events.
I tried to open the file but then I came to know that the file is only downloadable :/ WTF. You can’t open it on web server. But I don’t give up coz i have an other option that was rename the file with the payload ( every time you will not achieve that you want ) and again Unsuccessful.

I again opened the file in new tab to checkout it’s path and for executing payload but the web server only showed me
https://www.site.com/attachments/123456/download.png?id=12345
and file is ready for download.
I saw an id parameter in url with an integer value 😀
I just change the value and I am able to download the file of other teams 😀 3:) i.e
https://www.site.com/attachments/integer_value/download.png?id=integer_value
In Simple words I was able to download any file which is uploaded on there web server 😀
I agained made a Video POC and report them and Got a $300 as reward.

I know that the reward is low but it was their highest reward unfortunately! 😛
In the End I thanks to all my Masters
HAVE A NICE DAY!

Discover more from Security Breached Blog
Subscribe to get the latest posts sent to your email.
do you mind to share the site via email?