In recent years, Bug Bounties have gained significant popularity as a growing number of companies rely on crowdsourcing platforms to identify vulnerabilities within their systems. As such, the security of these platforms has become increasingly critical. Last year I uncovered a method to manipulate my ranking on the Bugcrowd Platform, and in this article, I will share how I did it, and what the implications could be.
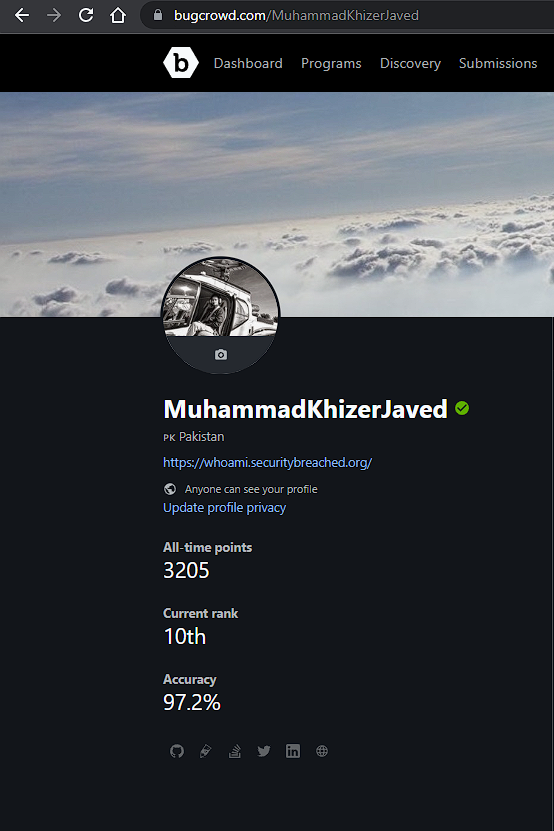
As a bit of background, I was testing the bugcrowd platform and I discovered that I was able to manipulate my rank on the platform by importing a bunch of reports using the Bugcrowd API and rewarding myself with points. Although these were demo points that didn’t reflect on my main profile public page, they were shown under my points total on my submissions page. and these demo points were then included in the platform’s ranking algorithm. By exploiting this I was ranked 10th on the platform, despite having only 3205 points. The person who used to be ranked 11th had 13789 points.
This was a serious issue, as an attacker with the ability to increase and modify data points could impact the ranking on the platform and potentially gain indirect financial benefits. For example, they could show a fake rank on public platforms, which could lead to reputational damage for the business and a loss of trust among customers.
Here are the technical details of the bug and how it worked?
Basically, for this, you needed to create two accounts on Bugcrowd, one Researcher Account and one Company Account. From your Tracker Account, create a Demo Program and obtain your API Credentials.
After that, You need to Craft an API request as per Bugcrowd’s official documentation to Create a Claim-able Submission for your researcher account here’s what it looked like.
import requests
headers = {
'accept': 'application/vnd.bugcrowd+json',
'authorization': 'Token <ADD-YOUR-API-TOKEN>',
'content-type': 'application/json',
}
data = '{"submission":{"source":"platform","title":"Security Breached","submitted_at":"2022-06-07T00:00:00.181Z","substate":"resolved","vrt_id":"server_side_injection.remote_code_execution_rce","priority":"1","researcher_email":"[email protected]"}}'
response = requests.post('https://api.bugcrowd.com/bounties/<YOUR-BOUNTY-UUID>/submissions', headers=headers, data=data)
print((response.text))
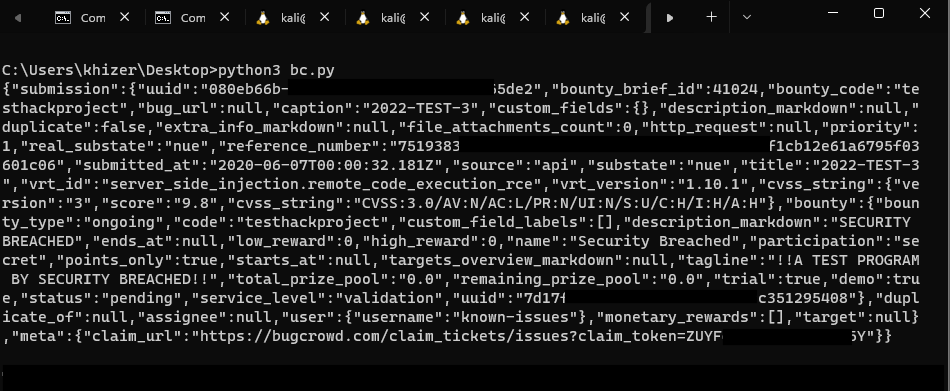
Once your request is successful you’ll receive an email with a claimable link to claim this submission and after that, you’ll be rewarded demo points which you’ll see in the sidebar of your submissions page.


Once I gathered enough demo points I could see the change in rank, for example, @MorningStar on Bugcrowd was ranked 10th but as I pushed my rank above his he was pushed down to 11th.

–
The impact of this bug was on the business side of Bugcrowd and others affiliated with it, as ranking is a part of the platform’s trust in other users and businesses. This issue could have led to reputational damage, loss of trust among customers, and financial losses.
I reported this issue to Bugcrowd, and they promptly fixed it. I appreciate their quick response and the importance they place on security. This experience has taught me the importance of responsible disclosure and the role of bug bounty programs in ensuring the security of our digital world.
In conclusion, as bug bounty programs become more prevalent, it’s important to remain vigilant and identify any potential vulnerabilities that could be exploited. I encourage researchers and companies alike to take security seriously and work together to make the internet a safer place.
Thanks for Reading!