
The POST explains What is Subdomain Hijack/takeover Vulnerability, What are the Impacts of the Vulnerability & How can You prevent such attacks, In addition to this I Tried my best to add the step by step guide about how to Identify & Exploit Vulnerable Subdomains Using 5 different services that includes,
Amazon Cloudfront
Heroku
Desk.com
Pantheon service
Github Pages
Hope This Post will help you guys to get a Clear POC about subdomain Takeover issues 🙂
Hey guys so I was looking at messages in my inbox and Realized that Most of my friends are sending In ScreenShots of random 404 errors on subdomains and asking about Possibilities of Subdomain Takeover… I don’t Know Much about the Subdomain Takeover Vulnerability! But Still i’m writing this…. LOL :v So Lets begin!
What is a Subdomain Hijack/Takeover Vulnerability?
A subdomain takeover is considered a high severity threat and boils down to the registration of a domain by somebody else (with bad intentions) By doing this, the hacker can take full control of the subdomains. Subdomain Takeover can be done by using external services such as Desk, Squarespace, Shopify, Github, Tumblr, and Heroku.
How it Works?
A service named ‘Work’ on your website which located at work.mysite.com hosted at third party like bitbucket, AWS Cloudfront or Heroku and the CNAME Points at this url mysitework.herokudns.com , and this service is not used on heroku , you just decided to use it and it expired or you did not claim it before but you added a dns entry pointing to heroku , so an attacker can claim it , then when you visit work.mysite.com you are redirected to attacker site on heroku or show Mac Content by the attacker.
Subdomain Takeover In a Sec?
- People register subdomains.
- Now they Point it to 3rd party apps/websites, Github pages, Heroku, S3, AWS are some examples.
- Sometimes they migrate or stop using the feature and forget to remove the name pointer.
- An entry exists at nameserver pointing to a page
- Create an account and claim that page.
- Done!
#OkThnxByeLoL
Here i’m Trying to share step by Step example of attack Identification & Exploitation!
- Subdomain Takeover Via Expired Cloudfront Distribution:
How to Identify Subdomain Takeover via Expired Cloudfront Distribution..
The Error? on The Subdomain the error will b something like This.

But that’s Not enough You need to Check the subdomain on Both HTTPS/HTTP if the same error Occur on Both then the subdomain can be Hijacked by creating an AWS cloudfront distribution and adding the subdomain in CNAME!
Simply login to your AWS Cloudfront account and create a New Bucket for the subdomain or use existing bucket

Now After that I visited Cloudfront Distribution options and created a New Cloudfront Distribution

I chooses the WEB option and In CNAME i added the link to the subdomain i.e sub.site.com

Next i simple Linked my Distribution to my S3 bucket and tadaaa, The Subdomain is NOw Yours
BlogPost related to This https://blog.securitybreached.org/2017/10/10/subdomain-takeover-lamborghini-hacked/
Wanna learn More about amazon? Read the Amazing amazon cookbook http://www.allitebooks.com/read/index.php?id=21483
2. Subdomain Takeover Using Heruko:
Error? The Vulnerable Subdomain might have an error similar to this one.

Now For verification further check the CNAME entry in DNS info it should be something similar to (site.herokudns.com) Then.. Create a New account on heruko.com and fill in the billing details ( Necessary ) then create a new app in your account 

after Creating the app Go to the app deploy menu and connect Your Deployment Method (Github, dropbox etc ) Then Go to settings and set build pack,
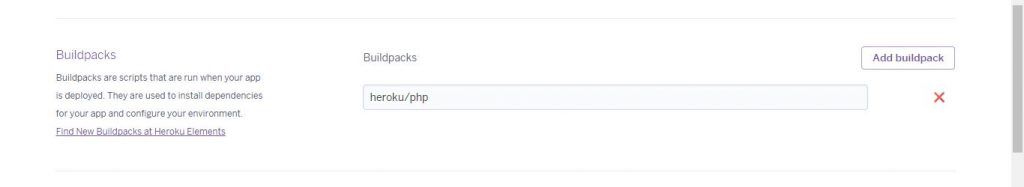
Now after that simply add the domain under the Build packs menu and then add content to the github and go back to deploy menu and clikc on deploy or enable automatic deploy Your all set.. The subdomain is now Yours

That’s all for Heroku!
3. Subdomain Takeover via Desk.com:
Error? the error on the subdomain that can be Hijacked via Desk.com will be something like.

To verify check the DNS entry for CNAME record it should be something like (site.desk.com)
after confirmation create an account on desk.com with the same CNAME and Then Go to settings and add the subdomain in Your Web address

after that enable it and the Subdomain will b yours 😉

That’s all for Desk.com
4. Subdomain Takeover via Pantheon service:
Error? the error on vulnerable subdomain should be like something like this:

i didn’t have screenShots related to this so Just gonna Post the steps 🙂
Steps:
- Signed up as client in Pantheon service.
- Created a Sandboxed domain as WordPress or Drupal.
- Added a credit card, then subscribed as ‘Professional’ to setup the sandboxed domain.
- Used a feature called “custom domains” to add the vulnerable subdomain to your account.
- Waited for the verification and building process to be finish.
- Boom You will be the admin of the subdomain.
5. Subdomain takeover Using Github Pages:
Error? The Error on the vulnerable subdomain should b like.

First You need to check the DNS info for CNAME Entry that should b something like (something.github.io)
after that visit the CNAME also it should show the same Error as The subdomain is showing.. Now You need to create a New repository in Your Github account matching with the CNAME of the website
then simply go to the settings of the repository

Now Scroll down to the GitHub Pages section. Press Choose a theme.. adn Select a New Theme for your guthub page.
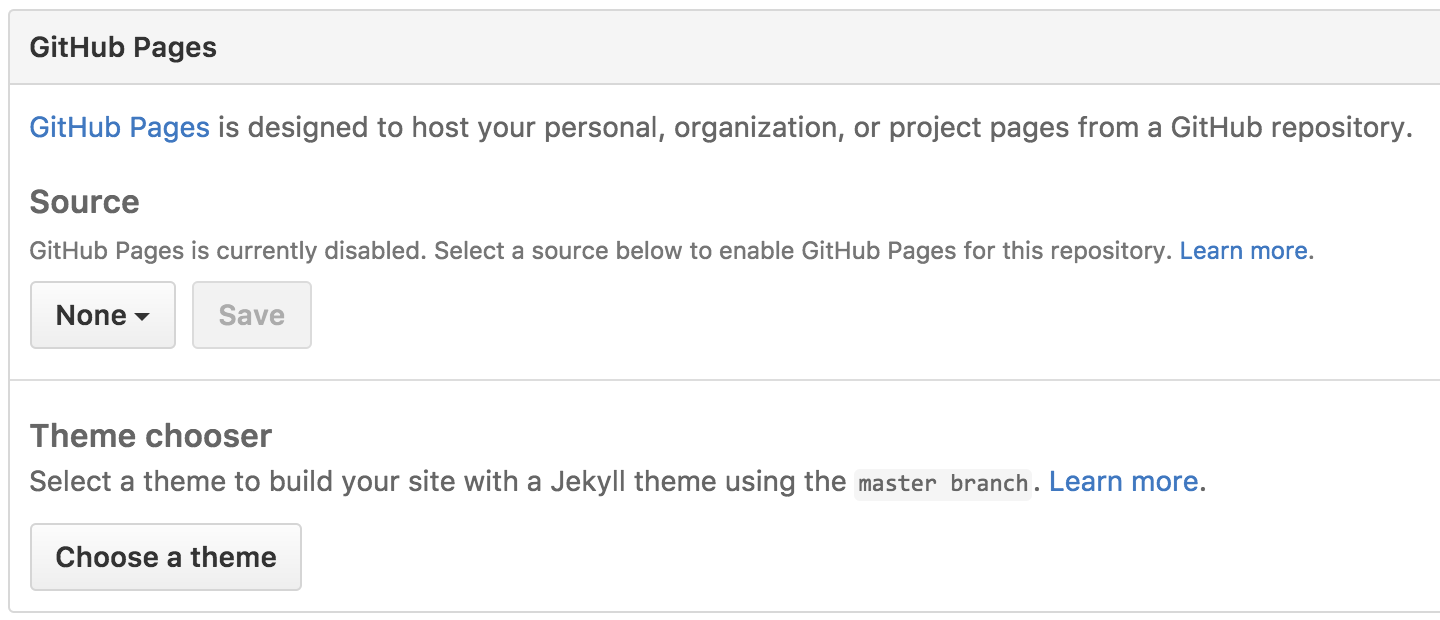
Pick a Theme you like
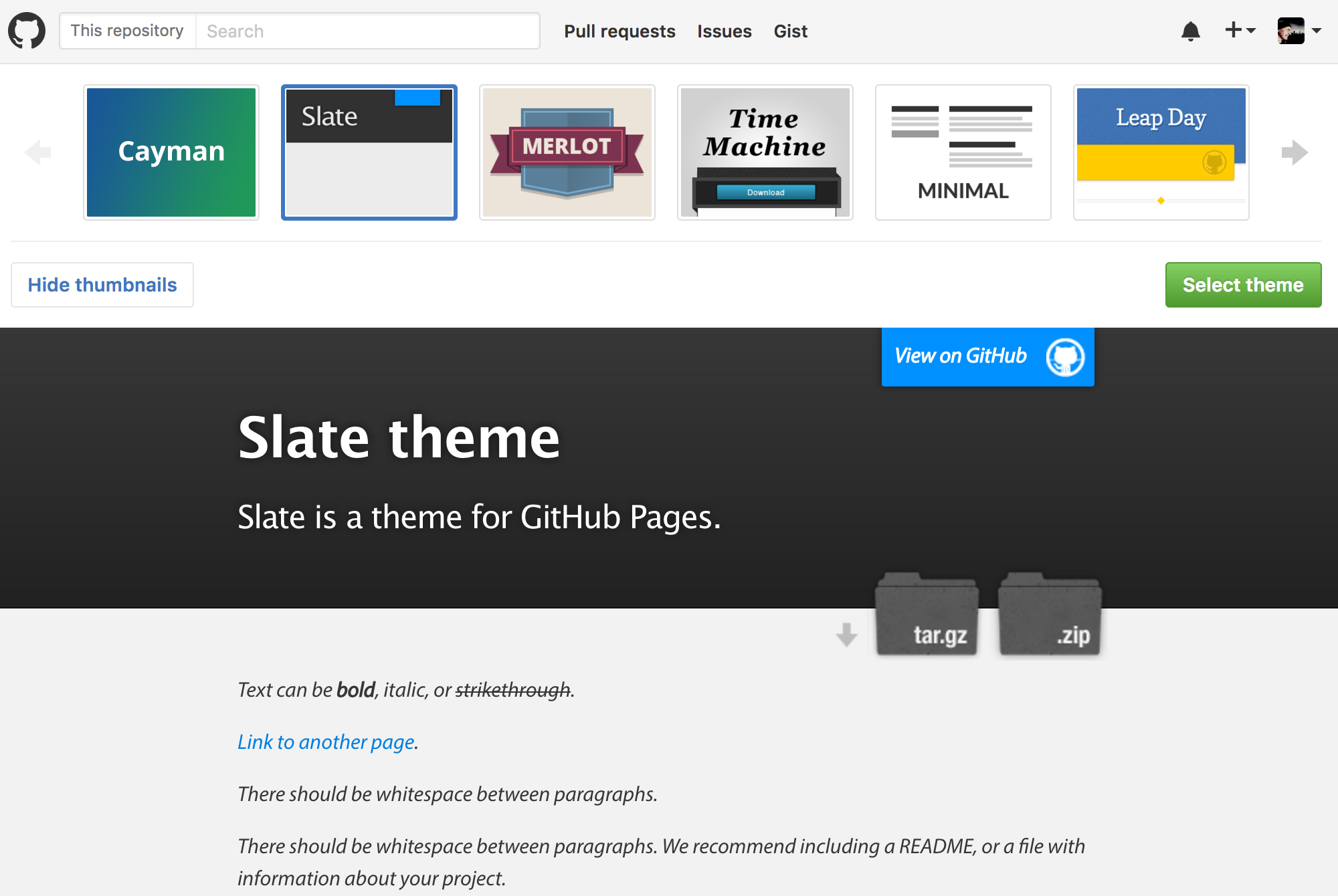
Now U can upload index and Other files to The repository and Edit them
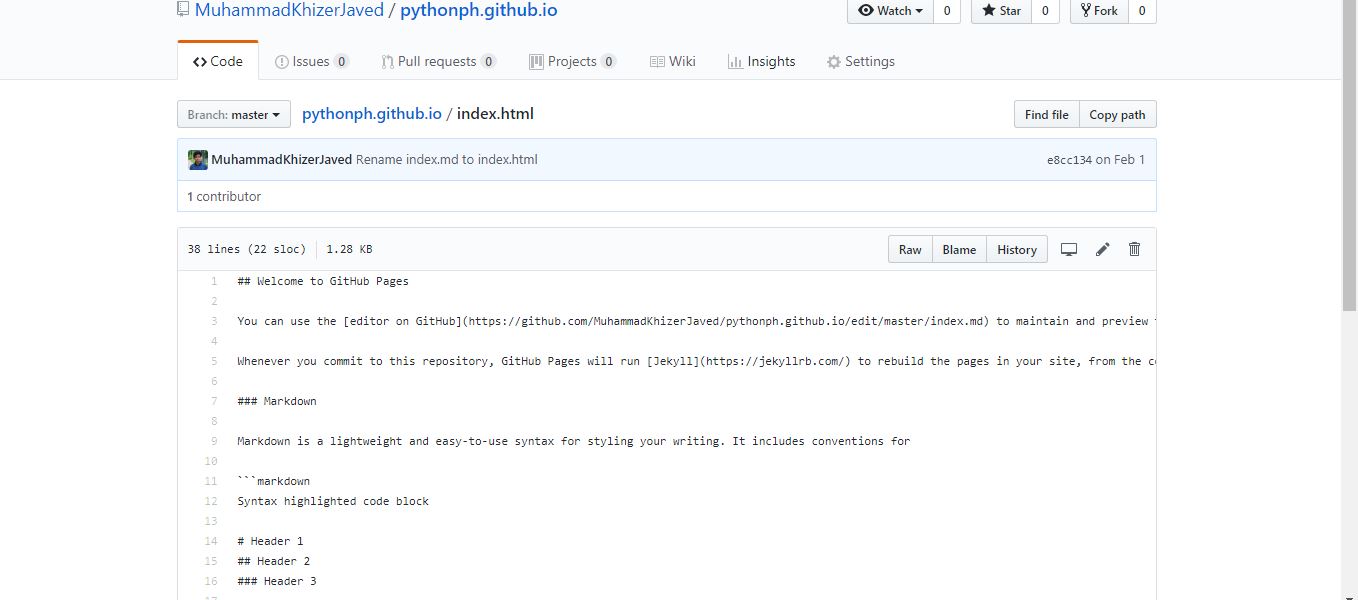
Now at the end Go to the setting of the repository again and Under Github pages choose custom domain and Add the domain that is Vulnerable to Takeover

Now Go to the subdomain and now it belongs to you 😉 wanna know more about it read https://help.github.com/articles/what-is-github-pages/

Now Lets Talk about Whats the impact of the issue and How can u defend against the issue?
- It is amazingly easy to sign up for a new account and claim the domain name.
- By having the domain, an attacker can build a complete clone of the site, add a login form that will redirect the user to a certain page, steal valuable credentials like admin accounts, steal cookies, or completely destroy the credibility of your company.
- It is a covert operation that even the domain owner won’t notice. The attacker won’t leave any traces; even your IDS cannot monitor this.
- Your Service Provider is unlikely to fix this in a feasible way.
- This Vulnerability can lead to Authentication bypass, CORS bypass & Many other high risk vulnerabilities.
How do you prevent this kind of attacks?
- If you’ve forgotten that your subdomain is pointed to an external service which you don’t update, then you just have to remove the DNS-configuration of the external service on your subdomain.
- Detectify’s domain monitoring
Detectify domain monitoring is a service for monitoring your subdomains for potential subdomain takeovers. It monitors changes within public DNS resolvers and warns you as soon as we detect any anomalies. Contact us on hello [at] detectify.com for more information. - Run a BugBounty Program lol We will look after for such issue for you 😛
Now For the Hunters Looking for some Scanners That can help you scan subdomains and Identify possibilities of Subdomain Takeover Vulnerability Here are some of them i frequently use
- https://github.com/nahamsec/HostileSubBruteforcer
- https://github.com/michenriksen/aquatone
- https://github.com/antichown/subdomain-takeover
- https://github.com/mhmdiaa/second-order
- https://github.com/guelfoweb/knock
- https://crt.sh/?q=%25domain.com
- https://censys.io/
- https://www.virustotal.com/#/domain/domain.com
etc 🙂
That’s what everything i know and I can share about the Subdomain Takeover vulnerability! hope It was helpful and easy to understand 🙂 Don;t forget to share 🙂
found these Memes related to the issue 😛


6 hosted to aid in subdomain finder before takeover is performed https://www.nmmapper.com/sys/tools/subdomainfinder/ including famous nmap’s dns-rute
bro i am unable to create account in desk it redirect me to salesforce website and dont ask me for cname for creation can you explain me how to takeover subdomain in desk.com as i read your above post but fou d difficulties in desk.com
hi, its acquired by salesforces so not possible anymore
What If i get Application Error on Heroku,,
Buddy for Cloudfront Distribution what if only in http we get The request could not be satisfied. And in https you get access denied amazon error msg.
Does that mean it’s not hijackable?
That means the Subdomain is Not Vulnerable 🙂 403/Frobidden/Access Denied means Its already owned and working well